Group-IB and INTERPOL: A Global Cybersecurity Milestone
In an age when cyber threats transcend borders and outpace traditional defenses, 2025 marked a pivotal moment in digital crime history. Group-IB, a global leader in cybersecurity innovation, and INTERPOL, the world’s largest international police organization, joined forces in an unprecedented operation: Operation Secure. This mission wasn’t just about arrests — it was a coordinated strike that shook the foundations of cybercrime networks across Asia-Pacific.
Why 2025 Marked a Turning Point in Cybercrime
2025 will be remembered as the year when cybercrime evolved from isolated attacks to a sophisticated, cross-border enterprise. Criminal groups deployed malware like Lumma, Risepro, and META Stealer to siphon sensitive data from individuals, businesses, and governments alike. The stolen data fueled an underground economy where login credentials, payment data, and crypto wallet keys became lucrative commodities on dark web markets.
In response, the world realized that fragmented efforts wouldn’t suffice. What was needed was a unified front — and Operation Secure delivered exactly that.
The Invisible War: Inside the World of Infostealers
Imagine software designed to lurk undetected on your device, quietly harvesting your personal and financial information. Infostealers are the silent predators of cyberspace. Once deployed, they collect everything from browser cookies to cryptocurrency keys, enabling criminals to commit fraud, launch ransomware attacks, or sell your data to the highest bidder.
The scale of these operations was staggering. Group-IB’s intelligence revealed sprawling infrastructures, linking thousands of malicious domains, IP addresses, and servers across continents.
Crafting Operation Secure: Strategy, Partners, Vision
Operation Secure wasn’t born overnight. It took months of meticulous planning under INTERPOL’s Asia & South Pacific Joint Operations Against Cybercrime (ASPJOC) framework. Group-IB, alongside partners like Kaspersky and Trend Micro, provided the technological muscle: advanced threat intelligence, digital forensics, and real-time monitoring.
The vision was clear:
-
Map and trace the cybercrime networks at their roots.
-
Coordinate law enforcement across 26 countries to act simultaneously.
-
Disrupt, dismantle, and disable the digital infrastructure of these criminal enterprises.
Group-IB’s Role in Unmasking Global Cyber Networks
Group-IB’s Unified Risk Platform played a crucial role. It consolidated data from millions of signals — malware signatures, phishing sites, botnet activity — and translated them into actionable intelligence. This allowed authorities to pinpoint not just individual operators, but entire syndicates.
💡 Expert Insight:
“The compromised credentials we identified were often just the first domino in a chain of attacks,” said Dmitry Volkov, CEO of Group-IB. “By removing that first domino, we could stop entire schemes from unfolding.”

Group-IB’s Role in Unmasking Global Cyber Networks
The Timeline of Takedown: How the Operation Unfolded
From January to April 2025, Operation Secure rolled out in phases:
🔹 Phase 1: Surveillance and mapping — Identifying the command servers, key players, and infrastructure nodes.
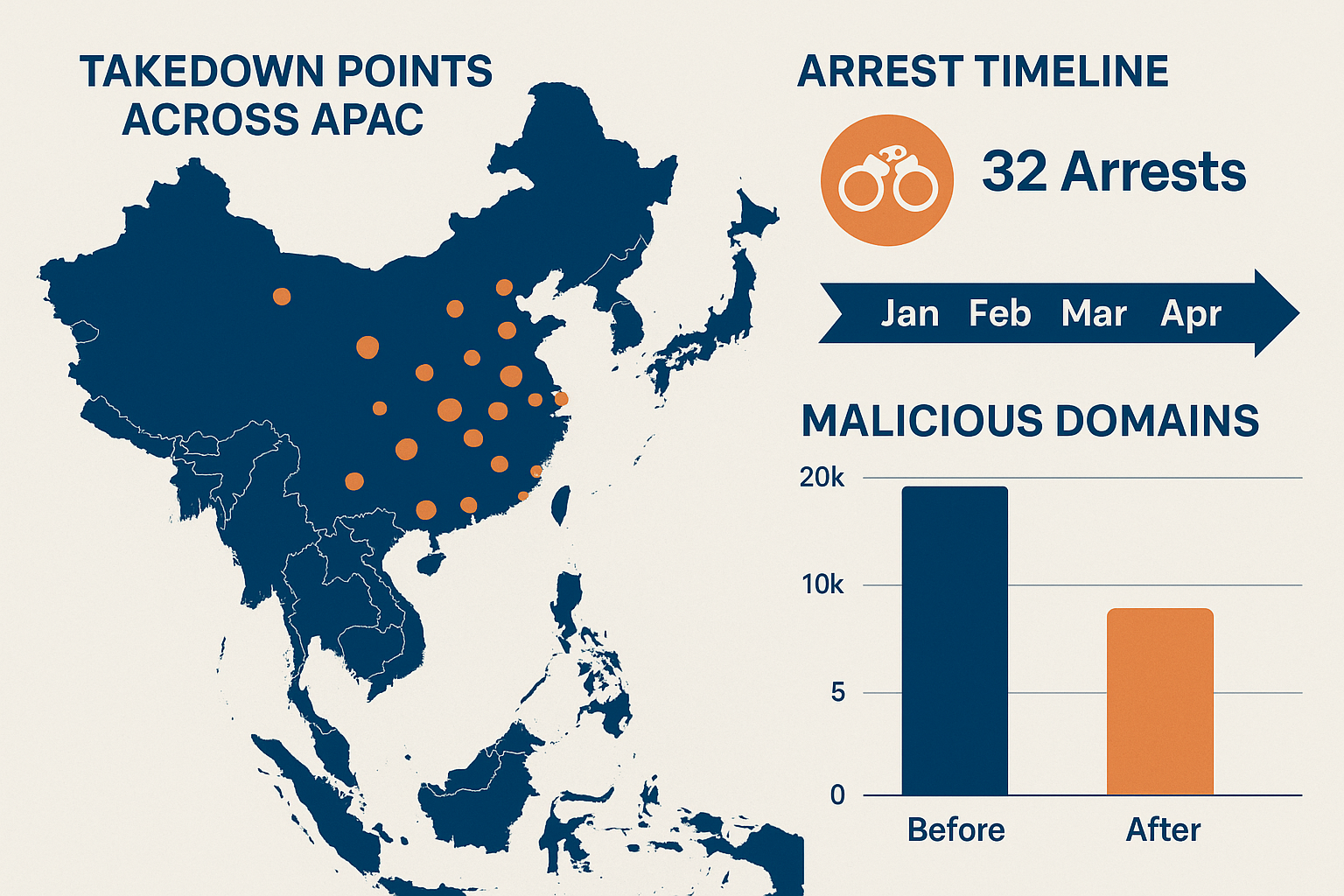
🔹 Phase 2: Coordinated takedowns — 20,000+ malicious domains and IPs taken offline; 41 servers seized.
🔹 Phase 3: Arrests and asset seizures — 32 arrests across APAC, millions in illicit funds, and thousands of SIM cards confiscated.
🔹 Phase 4: Victim outreach — Notifying 216,000+ victims to secure their data and accounts.
Dissecting the Tools of Cybercrime
The tools used by these cybercriminals were varied but deadly effective.
-
Lumma Stealer: Specialized in browser data theft.
-
META Stealer: Known for targeting cryptocurrency wallets.
-
Risepro: Focused on enterprise credentials, paving the way for BEC (Business Email Compromise) fraud.
Each acted as a gateway, opening doors to larger, more damaging exploits.
Vietnam’s Network: From Arrests to Recovery
Vietnam saw the highest number of arrests — 18 individuals linked to major infostealer distribution networks. Authorities recovered VND$300 million in illicit funds, SIM cards used in fraud, and fraudulent business registration documents. This wasn’t just about arresting people; it was about dismantling their ability to regroup.
The Hong Kong Command Servers Saga
Hong Kong emerged as a digital command center, hosting 117 servers used to control malware operations. These servers were spread across 89 different ISPs, illustrating how cybercriminals exploit fragmented hosting ecosystems to evade detection. Their takedown sent shockwaves through global cybercrime networks.

216,000 Victims Protected: What That Means
216,000 Victims Protected: What That Means
Numbers tell only part of the story. Each victim represents a person or business that avoided potential financial ruin, identity theft, or extortion. Operation Secure’s outreach efforts ensured these victims could take swift action, changing passwords, securing wallets, and protecting their digital lives.
The Power of Public-Private Partnerships
Operation Secure was proof positive that no single entity — not a nation, nor a corporation — can combat cybercrime alone. The synergy between Group-IB, INTERPOL, local law enforcement, and other cybersecurity firms created a model for future operations.
The Hidden Hurdles in Global Cyber Ops
Cross-border cooperation comes with challenges:
⚠ Differing legal frameworks
⚠ Varying levels of cybercrime readiness
⚠ Technical complexities of synchronizing actions across time zones
Yet, Operation Secure overcame these, setting a precedent for future collaboration.
How Group-IB’s Unified Risk Platform Redefined Defense
The platform integrated:
✅ Threat intelligence feeds
✅ Fraud detection systems
✅ Managed XDR (Extended Detection and Response)
✅ External attack surface monitoring
This holistic approach allowed law enforcement to act on complete pictures rather than fragments of data.
How This Operation Influences EUROPOL, AFRIPOL, Others
Operation Secure’s methodologies are already being applied in Europe and Africa, where Group-IB contributes to operations like Red Card — resulting in 300+ arrests — and supports EUROPOL’s advisory councils.
Balancing Privacy and Security in Cross-Border Ops
A critical consideration in such massive operations is ensuring that privacy rights aren’t trampled in the rush to secure digital spaces. Operation Secure struck this balance, operating within legal frameworks while achieving meaningful results.
What’s Next: The New Era of Cyber Defense
With AI, machine learning, and blockchain poised to play bigger roles, the next wave of cyber defense will be smarter, faster, and more adaptive. Group-IB and its partners are already investing in these technologies to stay ahead.
The Role of Infographics and Data Maps in Cyber Reporting
Visual storytelling — maps of takedowns, flowcharts of malware operations, before/after statistics — helps make complex operations understandable to the public and policymakers alike.
📌
interactive maps showing the takedown points across APAC, infographic of arrest timeline, and before/after charts of malicious domain counts.
A New Standard in Fighting Digital Crime
Operation Secure wasn’t just a victory. It was a blueprint — a reminder that collective action is the only way to safeguard our digital future.
FAQs
What was the main goal of Operation Secure?
To dismantle infostealer infrastructure, arrest operators, and protect victims globally.
Why was Group-IB’s role so critical?
Their threat intelligence linked digital clues to physical actors, making arrests and takedowns possible.
What’s the significance of the 216,000 victims protected?
Each represents a thwarted fraud, a prevented identity theft, or a saved business.
How did the operation impact cybercrime markets?
It disrupted trade in stolen data, causing major losses to criminal networks.
What’s next for similar operations?
Expansion into other regions, greater use of AI, and even tighter public-private cooperation.
for More tech news and Reviews stay connected ,stay up to date
https://www.youtube.com/@IhabMrTech
https://www.instagram.com/ihabmrtech/